Road Warriors - Setup Remote Access
Index
Intro
Remote access to the company’s infrastructure is one of most important and critical services exposed to the internet. IPsec Mobile Clients offer mobile users (formerly known as Road Warriors) a solution that is easy to setup and compatible with most current devices.
With this guide we will show you how to configure the server side on OPNsense with the different authentication methods e.g.
EAP-MSCHAPv2
Mutual-PSK + XAuth
Mutual-RSA + XAuth
…
Note
For the sample we will use a private ip for our WAN connection. This requires us to disable the default block rule on WAN to allow private traffic. To do so, go to and uncheck “Block private networks”. (Don’t forget to save and apply)

Sample Setup
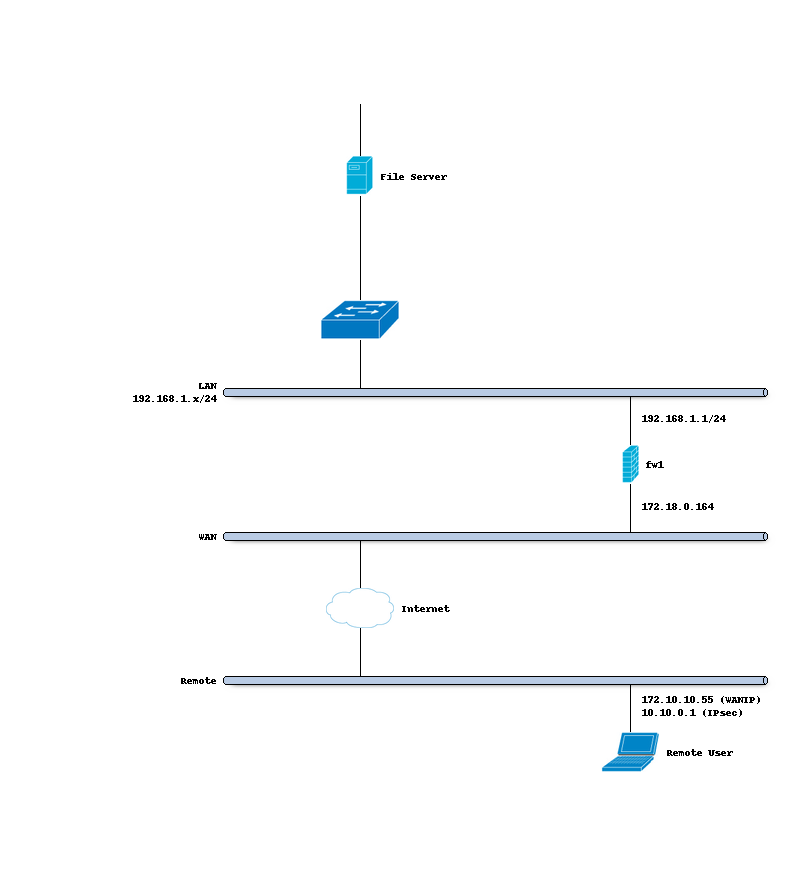
All configuration examples are based on the following setup, please read this carefully as all guides depend on it.
Company Network with Remote Client
Company Network
Hostname |
fw1 |
WAN IP |
172.18.0.164 |
LAN IP |
192.168.1.0/24 |
LAN DHCP Range |
192.168.1.100-192.168.1.200 |
IPsec Clients |
10.10.0.0/24 |
Firewall Rules Mobile Users
To allow IPsec Tunnel Connections, the following should be allowed on WAN.
Protocol ESP
UDP Traffic on Port 500 (ISAKMP)
UDP Traffic on Port 4500 (NAT-T)
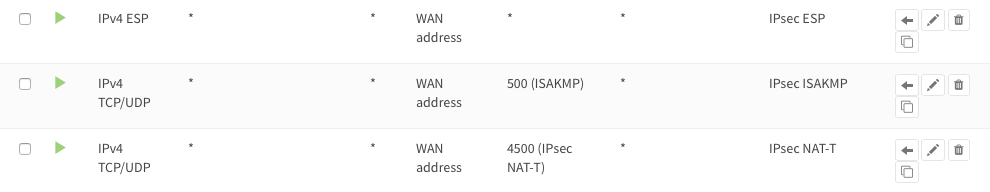
To allow traffic passing to your LAN subnet you need to add a rule to the IPsec interface.

VPN compatibility
In the next table you can see the existing VPN authentication mechanisms and which client operating systems support it, with links to their configurations. For Linux testing was done with Ubuntu 18.4 Desktop and network-manager-strongswan and libcharon-extra-plugins installed. As Android does not support IKEv2 yet we added notes for combinations with strongSwan app installed to have a broader compatibility for all systems. Mutual RSA and PSK without XAuth requires L2TP, since this legacy technology is very error prone we will not cover it here.
VPN Method |
Win7 |
Win10 |
Linux |
Mac OS X |
IOS |
Android |
OPNsense config |
|---|---|---|---|---|---|---|---|
IKEv1 Hybrid RSA + XAuth |
N |
N |
N |
tbd |
tbd |
N |
|
IKEv1 Mutual RSA + XAuth |
N |
N |
N |
tbd |
tbd |
||
IKEv1 Mutual PSK + XAuth |
N |
N |
N |
tbd |
tbd |
||
IKEv2 EAP-TLS |
N |
N |
N |
tbd |
tbd |
||
IKEv2 RSA local + EAP remote |
N |
N |
N |
tbd |
tbd |
||
IKEv2 EAP-MSCHAPv2 |
Y |
Y |
|||||
IKEv2 Mutual RSA + EAP-MSCHAPv2 |
N |
N |
N |
tbd |
tbd |
||
IKEv2 EAP-RADIUS |
Y |
Y |