Firewall
The firewall API offers a way for machine to machine interaction between custom applications and OPNsense, it is part of the core system.
Although the module does contains a basic user interface (in ), it’s mirely intended as a reference and testbed. There’s no relation to any of the rules being managed via the core system.
Tip
Use your browsers “inspect” feature to compare requests easily, the user interface in terms of communication is exactly the same as offered by the API . Rules not visible in the web interface () will not be returned by the API either.
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
alias |
add_item |
|
|
firewall |
alias |
del_item |
$uuid |
|
firewall |
alias |
export |
|
|
firewall |
alias |
get |
|
|
firewall |
alias |
get_alias_u_u_i_d |
$name |
|
firewall |
alias |
get_geo_i_p |
|
|
firewall |
alias |
get_item |
$uuid=null |
|
firewall |
alias |
get_table_size |
|
|
firewall |
alias |
import |
|
|
firewall |
alias |
list_categories |
|
|
firewall |
alias |
list_countries |
|
|
firewall |
alias |
list_network_aliases |
|
|
firewall |
alias |
list_user_groups |
|
|
firewall |
alias |
reconfigure |
|
|
firewall |
alias |
search_item |
|
|
firewall |
alias |
set |
|
|
firewall |
alias |
set_item |
$uuid |
|
firewall |
alias |
toggle_item |
$uuid,$enabled=null |
|
model Alias.xml |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
alias_util |
add |
$alias |
|
firewall |
alias_util |
aliases |
|
|
firewall |
alias_util |
delete |
$alias |
|
firewall |
alias_util |
find_references |
|
|
firewall |
alias_util |
flush |
$alias |
|
firewall |
alias_util |
list |
$alias |
|
firewall |
alias_util |
update_bogons |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
category |
add_item |
|
|
firewall |
category |
del_item |
$uuid |
|
firewall |
category |
get |
|
|
firewall |
category |
get_item |
$uuid=null |
|
firewall |
category |
search_item |
$add_empty=0 |
|
firewall |
category |
set |
|
|
firewall |
category |
set_item |
$uuid |
|
model Category.xml |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
d_nat |
add_rule |
|
|
firewall |
d_nat |
del_rule |
$uuid |
|
firewall |
d_nat |
get_rule |
$uuid=null |
|
firewall |
d_nat |
move_rule_before |
$selected_uuid,$target_uuid |
|
firewall |
d_nat |
search_rule |
|
|
firewall |
d_nat |
set_rule |
$uuid |
|
firewall |
d_nat |
toggle_rule |
$uuid,$disabled=null |
|
firewall |
d_nat |
toggle_rule_log |
$uuid,$log |
|
model DNat.xml |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
filter_base |
apply |
$rollback_revision=null |
|
firewall |
filter_base |
cancel_rollback |
$rollback_revision |
|
firewall |
filter_base |
get |
|
|
firewall |
filter_base |
list_categories |
|
|
firewall |
filter_base |
list_network_select_options |
|
|
firewall |
filter_base |
list_port_select_options |
|
|
firewall |
filter_base |
revert |
$revision |
|
firewall |
filter_base |
savepoint |
|
|
firewall |
filter_base |
set |
|
|
model Filter.xml |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
filter |
add_rule |
|
|
firewall |
filter |
del_rule |
$uuid |
|
firewall |
filter |
download_rules |
|
|
firewall |
filter |
flush_inspect_cache |
|
|
firewall |
filter |
get_interface_list |
|
|
firewall |
filter |
get_rule |
$uuid=null |
|
firewall |
filter |
move_rule_before |
$selected_uuid,$target_uuid |
|
firewall |
filter |
search_rule |
|
|
firewall |
filter |
set_rule |
$uuid |
|
firewall |
filter |
toggle_rule |
$uuid,$enabled=null |
|
firewall |
filter |
toggle_rule_log |
$uuid,$log |
|
firewall |
filter |
upload_rules |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
filter_util |
rule_stats |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
group |
add_item |
|
|
firewall |
group |
del_item |
$uuid |
|
firewall |
group |
get |
|
|
firewall |
group |
get_item |
$uuid=null |
|
firewall |
group |
reconfigure |
|
|
firewall |
group |
search_item |
|
|
firewall |
group |
set |
|
|
firewall |
group |
set_item |
$uuid |
|
model Group.xml |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
migration |
download_rules |
|
|
firewall |
migration |
flush |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
npt |
add_rule |
|
|
firewall |
npt |
del_rule |
$uuid |
|
firewall |
npt |
get_rule |
$uuid=null |
|
firewall |
npt |
move_rule_before |
$selected_uuid,$target_uuid |
|
firewall |
npt |
search_rule |
|
|
firewall |
npt |
set_rule |
$uuid |
|
firewall |
npt |
toggle_rule |
$uuid,$enabled=null |
|
firewall |
npt |
toggle_rule_log |
$uuid,$log |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
one_to_one |
add_rule |
|
|
firewall |
one_to_one |
del_rule |
$uuid |
|
firewall |
one_to_one |
get_rule |
$uuid=null |
|
firewall |
one_to_one |
move_rule_before |
$selected_uuid,$target_uuid |
|
firewall |
one_to_one |
search_rule |
|
|
firewall |
one_to_one |
set_rule |
$uuid |
|
firewall |
one_to_one |
toggle_rule |
$uuid,$enabled=null |
|
firewall |
one_to_one |
toggle_rule_log |
$uuid,$log |
Method |
Module |
Controller |
Command |
Parameters |
|---|---|---|---|---|
|
firewall |
source_nat |
add_rule |
|
|
firewall |
source_nat |
del_rule |
$uuid |
|
firewall |
source_nat |
get_rule |
$uuid=null |
|
firewall |
source_nat |
move_rule_before |
$selected_uuid,$target_uuid |
|
firewall |
source_nat |
search_rule |
|
|
firewall |
source_nat |
set_rule |
$uuid |
|
firewall |
source_nat |
toggle_rule |
$uuid,$enabled=null |
|
firewall |
source_nat |
toggle_rule_log |
$uuid,$log |
Concept
The firewall plugin injects rules in the standard OPNsense firewall while maintaining visibility on them in the standard user interface.
We use our standard ApiMutableModelControllerBase to allow crud operations on rule entries and offer a set of
specific actions to apply the new configuration.
Since firewall rules can be quite sensitive with a higher risk of lockout, we also support a rollback mechanism here,
which offers the ability to rollback this components changes.
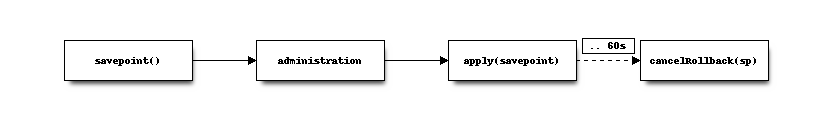
The diagram above contains the basic steps to change rules, apply and eventually rollback if not being able to access the machine again.
When calling savepoint() a new config revision will be created and the timestamp will be returned for later use.
If the cancelRollback(savepoint) is not called within 60 seconds, the firewall will rollback to the previous state
identified by the savepoint timestamp (if available).
Note
The examples in this document disable certificate validation, make sure when using this in a production environment to
remove the verify=False from the requests calls
Tip
The number of versions kept can be configured as “backup count” in . This affectively determines within how many configuration changes you can still rollback, if the backup is removed, a rollback will keep the current state (do nothing).
Administration example
Administrative endpoints are pretty standard use of ApiMutableModelControllerBase, the example below searches for
a rule named “OPNsense_fw_api_testrule_1”, when not found one will be added otherwise it will print the internal uuid.
Inline you will find a brief description of the steps performed.
1#!/usr/bin/env python3.7
2import requests
3import json
4
5# key + secret from downloaded apikey.txt
6api_key="3RhWOno+HwvtmT406I6zw8of8J6n9FOKlWK6U0B+K7stt/fDaJg7bjeF3QAshlScYqC+3o5THy3vQViW"
7api_secret="uaBk27NKhQCZSDpfAlG6YJ473MzvsCNiED6kzbYuykzU05fCRkcJADhDm5nxbZt8yREC74ZpvD/vbcEx"
8
9# define the basics, hostname to use and description used to identify our test rule
10rule_description='OPNsense_fw_api_testrule_1'
11remote_uri="https://192.168.1.1"
12
13# search for rule
14r = requests.get(
15 "%s/api/firewall/filter/searchRule?current=1&rowCount=7&searchPhrase=%s" % (
16 remote_uri, rule_description
17 ),
18 auth=(api_key, api_secret), verify=False
19)
20
21if r.status_code == 200:
22 response = json.loads(r.text)
23 if len(response['rows']) == 0:
24 # create a new rule, identified by rule_description allowing traffic from
25 # 192.168.0.0/24 to 10.0.0.0/24 using TCP protocol
26 data = {"rule" :
27 {
28 "description": rule_description,
29 "source_net": "192.168.0.0/24",
30 "protocol": "TCP",
31 "destination_net": "10.0.0.0/24"
32 }
33 }
34 r = requests.post(
35 "%s/api/firewall/filter/addRule" % remote_uri, auth=(api_key, api_secret), verify=False, json=data
36 )
37 if r.status_code == 200:
38 print("created : %s" % json.loads(r.text)['uuid'])
39 else:
40 print("error : %s" % r.text)
41
42 else:
43 for row in response['rows']:
44 print ("found uuid %s" % row['uuid'])
Tip
Since our model contains default values for most attributes, we only need to feed the changes if we would like to keep the defaults. In this case the TCP/IP version was IPv4 by default for example. In most cases one would like to set all relevant properties in case defaults change over time.
Apply / revert example
This example will disable the rule created in the previous example and apply the changes using a savepoint, since we’re not
calling cancelRollback(savepoint) it will revert after 60 seconds to the original state.
1#!/usr/bin/env python3.7
2import requests
3import json
4
5# key + secret from downloaded apikey.txt
6api_key="3RhWOno+HwvtmT406I6zw8of8J6n9FOKlWK6U0B+K7stt/fDaJg7bjeF3QAshlScYqC+3o5THy3vQViW"
7api_secret="uaBk27NKhQCZSDpfAlG6YJ473MzvsCNiED6kzbYuykzU05fCRkcJADhDm5nxbZt8yREC74ZpvD/vbcEx"
8
9# define the basics, hostname to use and description used to identify our test rule
10rule_description='OPNsense_fw_api_testrule_1'
11remote_uri="https://192.168.1.1"
12
13# search for rule
14r = requests.get(
15 "%s/api/firewall/filter/searchRule?current=1&rowCount=7&searchPhrase=%s" % (
16 remote_uri, rule_description
17 ),
18 auth=(api_key, api_secret), verify=False
19)
20
21if r.status_code == 200:
22 response = json.loads(r.text)
23 if len(response['rows']) > 0:
24 rule_uuid = response['rows'][0]['uuid']
25 r = requests.post("%s/api/firewall/filter/savepoint" % remote_uri, auth=(api_key, api_secret), verify=False)
26 if r.status_code == 200:
27 sp_response = json.loads(r.text)
28 # disable rule
29 r = requests.post("%s/api/firewall/filter/toggleRule/%s/0" % (remote_uri, rule_uuid),
30 auth=(api_key, api_secret), verify=False
31 )
32 # apply changes, revert to sp_response['revision'] after 60 seconds
33 r = requests.post("%s/api/firewall/filter/apply/%s" % (remote_uri, sp_response['revision']),
34 auth=(api_key, api_secret), verify=False
35 )
36 print("revert to revision %s in 60 seconds (%s changed)" % (sp_response['revision'], rule_uuid))
37 else:
38 print("rule %s not found" % rule_description)
Note
The savepoint will only revert this components changes, other changes won’t be affected by this revert, for example add an additional interface between savepoint and revert won’t be affected.